National Cyber League (Fall 2024)
Team "purdon't" placed 5th overall in the Fall 2024 Experienced Bracket.
Following the successes of purdon’t in the Fall 2024 National Cyber League, a smaller subset of the team opted to try our luck in the University of Connecticut’s CyberSEED 25 competition.
This competition followed a similar design to that of NCL, though it limited competitors to a seven hour competition window rather than NCL’s more generous three days. Additionally, the competition featured an incident response briefing challenge, where competitors had to probe an AI model and provide an executive-level presentation of their findings and possible business impact.
 Team purdon’t left to right:
Team purdon’t left to right:
Colin Saumure, Casey Gukasova, Kevin Archer, and David Racovan
CyberSEED is an annual cybersecurity competition where teams of four compete in a seven-hour sprint for a chance at a cash prize. Challenge categories include Open Source Intelligence, Cryptography, Password Cracking, Forensic & Log Analysis, Network Traffic Analysis, Reverse Engineering, Web Application Exploitation, and the Incident Response Briefing.
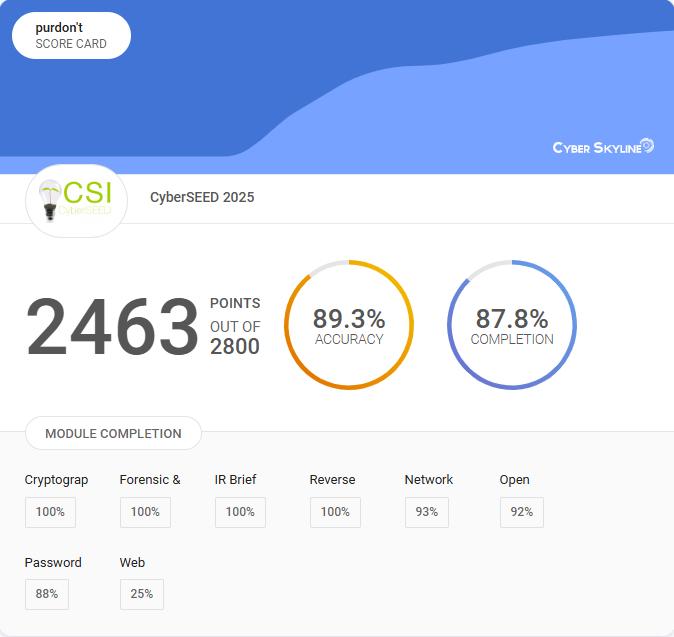 Team Scorecard
Team Scorecard
My efforts during the competition were primarily focused on the Cryptography, Log Analysis, and Network Traffic Analysis categories. Additionally, Casey and I shared the responsibility of designing and delivering the Incident Response briefing, from which we earned 298/300 points.
A good deal of my time was spent designing a custom log parser to extract data from a log file containing raw bytes. Although it might have saved me time, I tried to minimize my use of AI on this challenge except to guide me in the right direction. For example, I ran into some issues before realizing that the data was stored little-endian.
There was also a question within this challenge where you had to count the number of logs meeting certain criteria on a specific day. To do this, I ran a simple conversion of the Epoch timestamp into a DateTime object. However, I neglected the fact that when I was later checking the date value, it was being represented in UTC rather than the time zone used in the log. Although we lost some accuracy for this mistake, I was able to correct it and earn the points back.
The Network Traffic Analysis category had some interesting challenges, including a wireless packet capture taken on an airline and a challenge where we had to interpret an IoT protocol using an obscure datasheet.
Finally, there was a particularly interesting Cryptography challenge involving power traces. Competitors had to analyze several graphs of electrical power to determine the number of cryptographic rounds applied to data. From there, these graphs were used to pinpoint the algorithm used (AES) and the cryptographic function of AES that was being performed.